Pistolshrimp
Tenderfoot
- May 9, 2020
- 9
- 20
- Primary Interest:
- All Treasure Hunting
Hello all. Not sure if this is the right place for this. It's kind of a long post so I apologize in advance. Most of the length comes from the Methods section trying to explain what I am doing, if you wish you can skip that and still get the jist of the post. I tried to put it into a Spoiler tag but I don't see that option here so I put it in a quote so it can be skipped easily if so desired.
I am a GIS and Programming student who often finds myself drawn to mysteries and trying unique ways of solving them. While interesting I use them as ways to build skills, force me to think outside of the box, and ultimately to build my resume.
I am not a historian or a treasure seeker. I am not necessarily trying to crack the ciphers. That is probably outside my ability, and judging from the posts here, someone seems to "crack" them every couple of months. No shade of course, just that it is probably not worth the effort for me to go too far down that rabbit hole. I am posting on this site because it seems like you all are really knowledgeable and, perhaps for internet forums, uncharacteristically supportive. i have some conclusions at the bottom I would like to run by you all and see if you disagree or if there is something out there proving me wrong.
METHODS/EXAMPLES
What I have been doing is some cryptanalysis on the codes themselves. I built a program which inserts sentences into each of the ciphers and counts every time it fits and subsequent Trigrams it then creates. The sentences are made from an external file so I can essentially put in any text and it creates every sentence possible of lengths 1 - 10 for words adjacent to each other.
Again I am not looking at the plaintext at all, I am running thousands of sentences through each of the ciphers and looking for trends.
INITIAL DATA:
Depending on the length of the input text the program may takes several hours to run so I only have a couple of runs.
I ran 2 different texts, the first the successful solution to cipher 2, and for the second I tried to find some text that seemed as far as I could get from what is contained in the ciphers: the first two paragraphs of a review of one of Ariane Grande's albums.

I have highlighted the part that I think is most interesting. The Trigrams found.
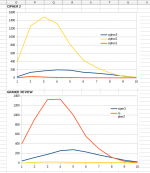
Here's are a couple of graphs that may help visualize things. (I apologize for the very poor quality graphs, I should have normalized the data and worked on colors to increase readability.)
So interestingly cipher 2 creates a high common Trigram count even when using the wrong key to decipher it. (Unless Beale was an Ariana Grande fan and hid a secret review of her album in his cipher.) Additionally they both follow the same slightly left leaning bell curve. Cipher's 1 and 3 also produce similar curves no matter what text is put thought (obviously only 2 data points at the moment).
Conclusions I am leaning towards.
1. Ciphers 1 and 3 may not be real. They do not follow the expected pattern set by cipher 2.
2. If ciphers 1 and 3 are real they differ quite a bit from cipher 2 in construction. With 1 differing much more than 1.
3. If cipher 1 is real this high difference is MAY be accounted for by not being English sentences but rather lists of names. Implying cipher 1 is actually cipher 3.
I am writing all this because you all are probably the experts on Beale and hope to get your thoughts. None of this is conclusive; I need to do more runs and compute a p-value to see if these results are greater than chance, but so far they look like they are.
What are your thoughts on my conclusions?
I am a GIS and Programming student who often finds myself drawn to mysteries and trying unique ways of solving them. While interesting I use them as ways to build skills, force me to think outside of the box, and ultimately to build my resume.
I am not a historian or a treasure seeker. I am not necessarily trying to crack the ciphers. That is probably outside my ability, and judging from the posts here, someone seems to "crack" them every couple of months. No shade of course, just that it is probably not worth the effort for me to go too far down that rabbit hole. I am posting on this site because it seems like you all are really knowledgeable and, perhaps for internet forums, uncharacteristically supportive. i have some conclusions at the bottom I would like to run by you all and see if you disagree or if there is something out there proving me wrong.
METHODS/EXAMPLES
What I have been doing is some cryptanalysis on the codes themselves. I built a program which inserts sentences into each of the ciphers and counts every time it fits and subsequent Trigrams it then creates. The sentences are made from an external file so I can essentially put in any text and it creates every sentence possible of lengths 1 - 10 for words adjacent to each other.
For instance take, "I HAVE DEPOSITED IN THE COUNTY OF BEDFORD ABOUT FOUR". My program would create a sentence for each word, then make sentences for "I HAVE", "HAVE DEPOSITED", "DEPOSITED IN" and so on until it would use the whole thing. It would do this for all the words in the entire text.
Then it would try to fit every sentence into the cipher and count the times it fits and the amount of accidental Trigrams it creates. Trigrams being three letters in a row that are common in other words and which may or may not be other words themselves, for instance ("THE", "AND", "NTH", "ERE").
Lets take my earlier sentence as an example: The entire word block, "I HAVE DEPOSITED IN THE COUNTY OF BEDFORD ABOUT FOUR" fits into the Third Cipher 25 times, changing every other number to the assigned letter. It only won't fit when it would have to re-write over a letter, IE when the program tries to assign two different letters to the same number. Of those 25 successful fits only 3 of them create extra common Trigrams.
For here is one return: Trigams found = 'TIO' and 'ORT'.
Puesdo PlainText:
IHAVEDEPOSITEDINTHECOUNTYOFBEDFORDABOUTFOURS****O***D**TIO****O*****E*********O**H**DI**T*****D**DS***OD****SAO**O*TC**HUF*NB**OHO*FD***E********************FT*E****U***S*F********************E********FE****S*O*P**U**D***VTB********D***IH*****A***O**I******UDH*****O***TRA********FDA*O**S*A***UE**********Y**DH*T**B****H*****D**************DODF*****S**B*****F************OED**E*SBORT*******H************F*O*D****BVDS**F****************E*B***D***********N*****VA*B****DS************S**BT*F**Y**U*E**O********F**********A*******NE************************DO****BD*EO*******ED****D*F**S**********************U*************
As you can see while this does make Trigrams and things that look like they could be English words it also produces nonsense strings like "BVDS". My program does not filter out these nonsense stings. I typically don't even look at the plaintext, I just printed it out to better explain the process.
What is interesting, at least to me, is if I take the same sentence and run it though Cipher 2. This is essentially my control.
Attempts that include 'I HAVE DEPOSITED IN THE COUNTY OF BEDFORD ABOUT FOUR':2
Attempts which include a Trigram not already in Key: 1
Trigrams: ['AND', 'ION', 'VER', 'ONE', 'INE', 'UND']
Puesdo PlainText:
IHAVEDEPOSITEDINTHECOUNTYOFBEDFORDABOUTFOUR***E*FRO***FO***I***E***VA***N*RV*U*****F****E****HE**RF***O******O******F***O**N***TI*****E*ON*I***O****YT***E*****E**********S**E*IV********E***R**H**E*******F****D**O***C***I*TC***T*NHU*DRE****F*U**EE**O**D******D*****I*TY*I*H**U***ED**D**E*VE**UND***SI*VER***OS**E*NOV******E**INE*EEN**E****N******D**E******E**T*EN*YO****D*ON*I*************N****RED*N***VE**O*ND*OF*O*****T***V**U***ED******H*YE**H******V*R*******E*******N**I**T*O****NE******ETO**V************ION***V********HI*TE**R****AND*O*******EA**VE**S**U***Y**C**D*N**O**O***********OV****H*V*******OU***Y***ED******ONEA*D*H*VE*****RE*TON*O*ID**O*E******C*V********O*H******ER****ER*NE*****I****HC******O*****Y*F***V*****O***T*****FIC***Y***********F*N*IN*I*
Only 1 solution works that provides readable common Trigrams - the real solution.
Again I am not looking at the plaintext at all, I am running thousands of sentences through each of the ciphers and looking for trends.
INITIAL DATA:
Depending on the length of the input text the program may takes several hours to run so I only have a couple of runs.
I ran 2 different texts, the first the successful solution to cipher 2, and for the second I tried to find some text that seemed as far as I could get from what is contained in the ciphers: the first two paragraphs of a review of one of Ariane Grande's albums.

I have highlighted the part that I think is most interesting. The Trigrams found.

Here's are a couple of graphs that may help visualize things. (I apologize for the very poor quality graphs, I should have normalized the data and worked on colors to increase readability.)
So interestingly cipher 2 creates a high common Trigram count even when using the wrong key to decipher it. (Unless Beale was an Ariana Grande fan and hid a secret review of her album in his cipher.) Additionally they both follow the same slightly left leaning bell curve. Cipher's 1 and 3 also produce similar curves no matter what text is put thought (obviously only 2 data points at the moment).
Conclusions I am leaning towards.
1. Ciphers 1 and 3 may not be real. They do not follow the expected pattern set by cipher 2.
2. If ciphers 1 and 3 are real they differ quite a bit from cipher 2 in construction. With 1 differing much more than 1.
3. If cipher 1 is real this high difference is MAY be accounted for by not being English sentences but rather lists of names. Implying cipher 1 is actually cipher 3.
I am writing all this because you all are probably the experts on Beale and hope to get your thoughts. None of this is conclusive; I need to do more runs and compute a p-value to see if these results are greater than chance, but so far they look like they are.
What are your thoughts on my conclusions?







